Is a Hidden WiFi Network Secure? (Hidden SSID)
Table of Contents
When performing a WiFi network security audit, it is important to identify hidden network names, also known as ESSID under the 802.11 standard.
Before connecting, or even attempting to connect to a wireless network, its name must be known. Furthermore, in case of WPA/WPA2 security type networks, an ESSID is required to verify the Pre-Shared Key (PSK), the encryption key.
Usually, WiFi network access points send their network name as one of the Information Elements that are included in some of the management type frames, more precisely, the beacons (type=0x00, subtype=0x05) with the information element which identifier is 0. This parameter structure is shown as follows:
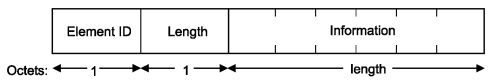
For some years, the main manufacturers of WiFi devices operating on AP mode have been giving the option to configure the devices to hide their network names. This has been implemented as a security feature to prevent unwanted connections, since the network name is one of the required parameters to establish connection, although it has an important design flaw.
How to Obtain Hidden WiFi Network Name (ESSID) Length
Even when a network name is not provided, most devices operating on AP mode send the Information Element that includes the network name as a field containing a hexadecimal 0x00 value, as well as its length.
This piece of information is a first approximation to obtaining the hidden WiFi network name. This is also frequent in corporate environments, where network names are usually self-explanatory or follow a certain deducible pattern, therefore it is possible to predict all network names from one of them by knowing their length.
How to Obtain a Hidden WiFi Network Name (ESSID)
A client device trying to connect to a WiFi network sends a Probe Request type frame to the AP and requests certain information from the AP while sending client device information to the AP. This information is sent to the client device through another frame known as Probe Response (type=0x00, subtype=0x05). This information exchange initiates the association process of the station with the AP.
The network name is part of the information sent to the network and since these types of frames are usually not encrypted or protected, it is possible to obtain the network name by monitoring WiFi traffic with a sniffer until a registered client connects to the network, or forcing an already connected client to reconnect to the network.
Hidden WiFi Network Attacks
After some research we have found that there is an Information Element message that can be sent through the Probe Request type frames, used for a Station to request another IE to a different Station. It is then possible to request an AP that is not transmitting the network name to kindly send us that parameter in a Probe Response packet.
Since this is an optional Information Element which is hardly ever used (although it is defined in the 802.11-2007 standard), most AP firmwares have not implemented or have completely ignored its behavior, therefore the use of this “functionality” is highly limited. We have tested several models and we have concluded that this flaw is found in older Android versions when using an external software to create an AP, as well as in some older D-Link models.
Is a Hidden WiFi Network Secure?
Not at all. Hiding a SSID only offers a layer of “security through obscurity”, and if the router has a vulnerable firmware or there is at least one client connected to the network, then the WiFi network name can be obtained as it’s expose to WiFi packet capture software. With Acrylic Wi-Fi Home or with Acrylic Wi-FI Professional, the hidden networks appear in red once they are identified through the WiFi network traffic automatic analysis.
This article is part of a series of articles about WiFi setup for teleworking and small offices