Attacks on WPA Enterprise infrastructures with hostapd-WPE
The previous article outlined the cross-compilation and installation process of hostapd-WPE for OpenWrt Barrier Breaker. This article continues detailing the configuration and execution of hostapd-WPE for OpenWrt, aiming in conducting security tests on WPA Enterprise environments 802.11x.
Hostapd-WPE allows conducting IEEE 802.11x (WPA Enterprise) server impersonation attacks in order to obtain client credentials, but also implements Cupid attack, allowing to exploit heartbleed vulnerability (CVE-2014-0160) on client connections over EAP-PEAP/TLS/TTLS.
- 802.11a (5Ghz) interface configuration
It has been verified that certain devices don’t bring up the Wi-Fi 802.11a interface by default on boot up, so it needs to be configured manually. In first place, the available interfaces with be checked by running the following command. iwconfig Alternatively the iw command can be executed in order to identify the interfaces associated with physical devices: iw dev
If the 802.11a interface is not up, It will need to be configured manually. All the available physical interfaces can be listed executing the following command. iw phy After executing iw phy, all physical interfaces will be listed detailing the characteristics of each device. Finally it will be possible to manually bring up the interface. In our case the physical interface (phy0) will be brought up with name wlan0 in managed mode. iw phy phy0 interface add wlan0 type managed The interface can be configured in monitor mode by modifying the type parameter and setting the monitor value instead of managed. The available options are listed below: managed, ibss, monitor, mesh, wds
- Creating custom self signed SSL certificates (Optional)
Although default certificates have been provided with the package, it will be possible to generate our own self signed certificates by executing the bootstrap script included in bootstrap/certs directory. Openwrt does not have any package including openssl command line tools, consequently the bootstrap script will need to be executed in the Linux host environment.
The certification authority parameters and the server certificate parameters can be configured by modifying ca.cnf and server.cnf files.
The parameters that usually will need to be modified are shown in the following image 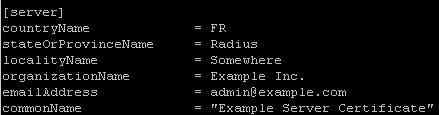 After execution the private keys and certificates will be created. In order to use them with hostapd-WPE for OpenWrt it will be necessary to copy ca.pem, server.pem, server_no_pass.key and dh to the device folder /usr/local/etc/hostapd-wpe/certs
After execution the private keys and certificates will be created. In order to use them with hostapd-WPE for OpenWrt it will be necessary to copy ca.pem, server.pem, server_no_pass.key and dh to the device folder /usr/local/etc/hostapd-wpe/certs
- Hostapd-WPE execution
To execute hostapd-wpe a configuration file will need to be provided. The package includes two functional configuration files that can be used to set up 802.11b/g/n (hostapd-wpe-bgn.conf) and 802.11a/n (hostapd-wpe-an.conf) fake WPA Enterprise networks.
The most relevant configuration parameters are discussed below:
- Interface
The interface parameter specifies the interface used to bring up the Wi-Fi network. If your 802.11b/g/n interface is configured as wlan0 this parameter will need to be modified in (hostapd-wpe-bgn.conf). The same applies to the 802.11 ac interface in hostapd-wpe-an.conf interface=wlan0
- SSID
The network name (SSID) can be set up modifying the ssid parameter. ssid=Acrylic Wifi
- Channels
The network channel can be set up by modifying the channel parameter. It needs to be noted that the channels will be different in 2,4 Ghz (802.11 b/g/n) and 5Ghz(802.11a) networks. channel=6
- Certificates and private key.
The following options specify the locations of the certificate and private key files generated after executing the bootstrap script. These parameters will need to be modified if you used other directory to store the certificate and private key files. ca_cert=/usr/local/etc/hostapd-wpe/ca.pem server_cert=/usr/local/etc/hostapd-wpe/server.pem private_key=/usr/local/etc/hostapd-wpe/server_no_pass.key private_key_passwd=whatever dh_file=/usr/local/etc/hostapd-wpe/dh
- Log files
The wpe_logfile parameter specifies the log file where the client hashes will be stored after a successful client authentication. The client hashes will be used later in the cracking phase in order to recover the client credentials. wpe_logfile=./wpe_an.log By default the log file is stored in the working directory.
- Running hostapd-WPE for OpenWrt – 802.11b/g/n access point setup
hostapd-wpe-bgn.conf configuration file. The -dd option enables debug mode, which displays more information during client authentication. Hostapd-wpe -dd /usr/local/etc/hostapd-wpe/hostapd-wpe-bgn.conf As users authenticate hashes will be shown on screen: 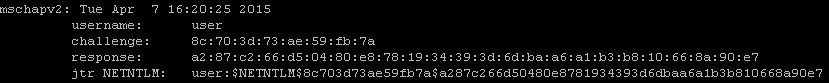
- 802.11a/c access point setup
To set up an 802.11ac access point the default (hostapd-wpe-an.conf) configuration file can be used. The following command will initiate an 802.11ac network.
Hostapd-wpe -dd /usr/local/etc/hostapd-wpe/hostapd-wpe-an.conf
Recovering client credentials by cracking WPA Enterprise hashes
In first place the client hashes will need to be recovered from the log files. The hashes will be saved in the hashes_john.txt file.
cat wpe_bgn.log
grep “jtr NETNTLM” sed ‘s/
[ ]*jtr NETNTLM:[ ]*//’ > hashes_john.txt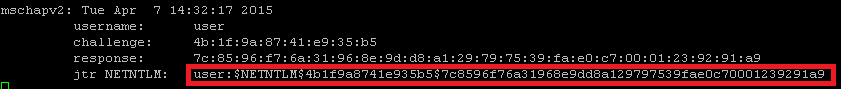 Alternatively the cracking can be done using asleap specifying the challange and response values. The following command uses John the Ripper to perform modification on dictionary words and redirecting the output to asleap. Note that the dash after the -W parameter allows John the Ripper output to be piped into asleap.
Alternatively the cracking can be done using asleap specifying the challange and response values. The following command uses John the Ripper to perform modification on dictionary words and redirecting the output to asleap. Note that the dash after the -W parameter allows John the Ripper output to be piped into asleap.
john –wordlist=/usr/share/john/password.lst –rules –stdout
asleap -C 5d:7c:53:ac:39:0d:44:c8 -R
0b:ee:1a:9e:0c:c4:98:aa:55:1c:69:92:62:e5:d5:82:60:0c:e8:81:01:81:23:91 -W –
The cracking can also be done with Aircrack or CowPatty.
References:
- https://blog.opensecurityresearch.com/2012/04/capturing-and-cracking-peap.html
