
Acrylic Suite
Keep WiFi simple
Thousands of users -from beginers to professionals- trust Acrylic to easily enhance their WiFi
Explore our productsWiFi analysis, site survey & troubleshooting
Simplicity is our commitment
Fast & Easy
Get network diagnostics from your laptop or tablet.
Easy to use
Visualize all results in an intuitive and user-friendly way.
Reliable
Reduce WiFi network downtime and increase performance.
Acrylic Suite solutions
Planning & site survey
Acrylic Wi-Fi HeatmapsAnalysis and troubleshooting
Acrylic Wi-Fi AnalyzerAdvanced sniffer
Acrylic Wi-Fi SnifferSIGINT & GEOINT
Acrylic Wi-Fi LEABluetooth analysis
Acrylic BLE AnalyzerHeatmaps
Planning & site survey
All stages of a WiFi infrastructure analysis at your disposal.
Design and plan your WiFi deployment from scratch. Get assessment on already deployed networks.
Visualize all results graphically, obtain intuitive metrics and generate customized reports.
- Design and plan a WiFi network from scratch.
- Site survey, coverage and network quality heatmaps.
- WiFi quality. Identify and fix all problem areas of your WiFi infrastructure.
- Create customized and editable reports.
- WiFi 7 support in all frequency bands
And many other features...
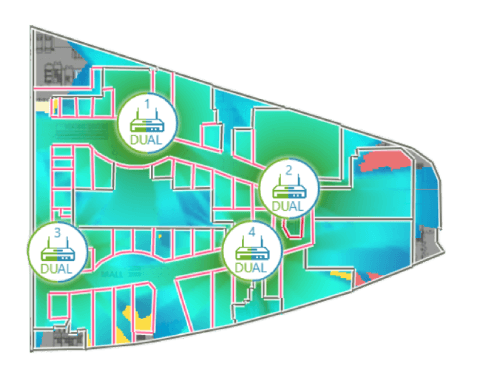
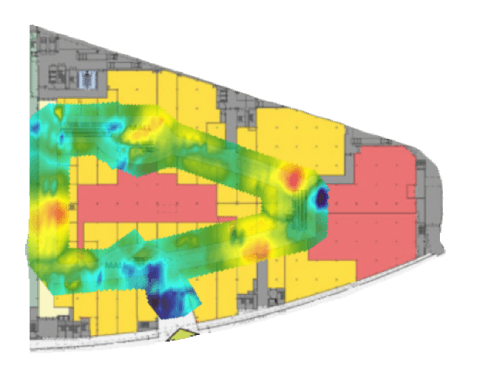
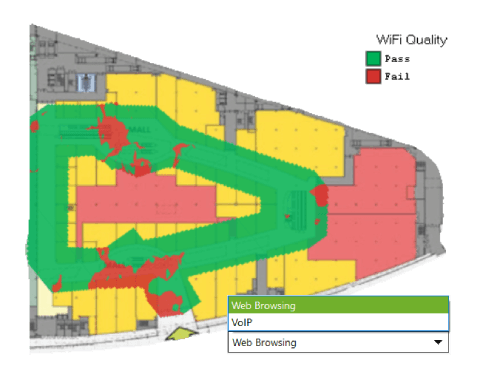
Analyzer
Analysis and troubleshooting
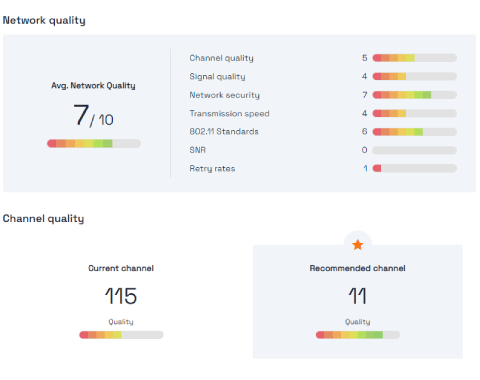
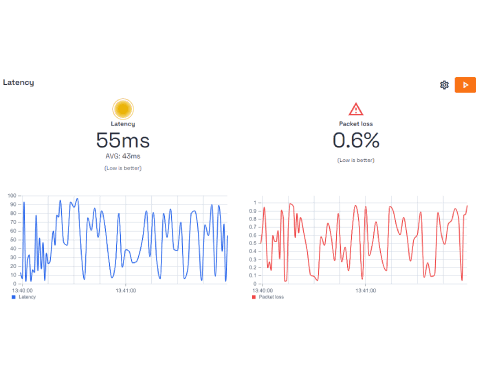
Discover what is happening on your Wi-Fi network, run metrics, and measure the performance. Resolve issues and get improvement recommendations.
Simple and user-friendly. Modern and intuitive design that helps less experienced users.
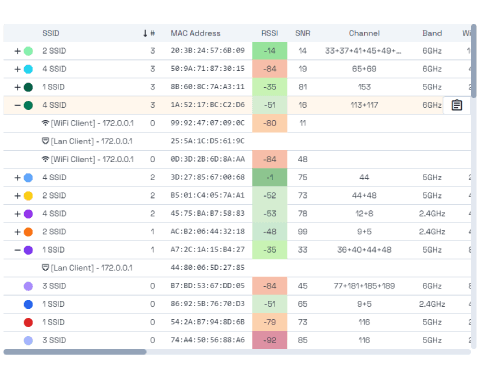
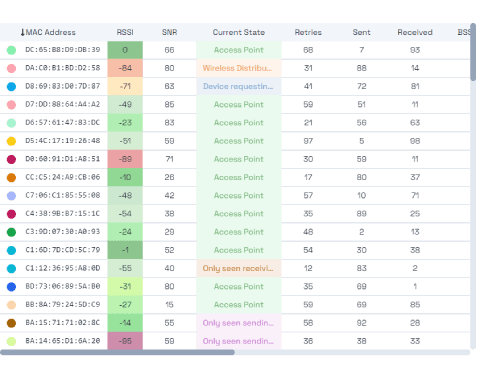
- Analyze your network, identify clients, and measure their performance in real time.
- Troubleshoot and get recommendations. Forget about slow connections.
- Detect APs and devices (Routers, tablets, phones, laptops, ...)
- WIFI 7 support in all frequency bands
And many other features...
Sniffer
Next-level packet capture
Capture all wifi packets coming from any device in a WiFi environment.
Analyze the WiFi networks protocol and performance at low-level.
The perfect complement to Acrylic Wi-Fi Analyzer, Heatmaps, and Wireshark.
- Monitor mode improved.
- Uses inexpensive and common hardware
- Third party integration. Use your favorite software.
- No complexity. No configuration required
And many other features...
Professionals agree:
Many powerful features and easy to use.
We designed new wifi deployments on all of our warehouses using Acrylic Wi-Fi Heatmaps. Now we use it to periodically validate the performance in all our facilities.

Klaus Andersen
Networking Engineer
All our technicians rely on Acrylic Wi-Fi Analyzer to solve problems arising in our customers' wireless networks.

Priya Chopra
Facilities Manager Network Coverage
With the Acrylic Wi-Fi Sniffer we have been able to monitor all clients connected to our WiFi networks and identify issues in the protocol configuration we were using.

Alex Miller
Network Administrator



